Achieving robust security compliance involves not only adhering to jurisdictional laws and industry regulations but also incorporating compliance frameworks into your strategy. The NIST Cybersecurity Framework contains best practices and controls for cybersecurity risk management, enabling organizations to address diverse risks and secure their data and systems. To guide your implementation of the NIST CSF, this article will take you through the components of the framework, the compliance process, and the equivalent maturity levels that your organization can attain upon being compliant. Read on to learn more:
What is the NIST CSF?
Established by the National Institute of Standards and Technology, the NIST CSF provides guidelines for managing risks through a set of high-level cybersecurity outcomes that organizations should aim to achieve. These outcomes are organized by functions, which make up the majority of the components of the framework:
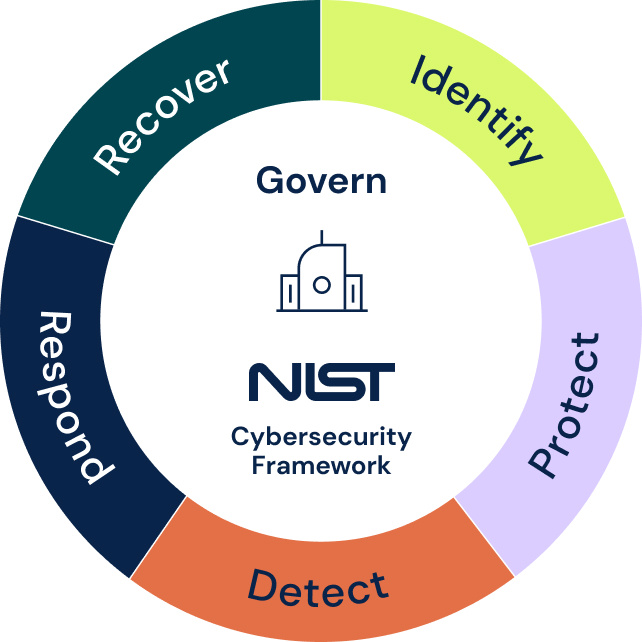
NIST CSF Core Functions
- Govern – Cybersecurity risk management strategies, objectives, and policies are established, communicated, and monitored.
- Identify – The organization’s cybersecurity risks and their corresponding impacts are identified, understood, and evaluated.
- Protect – Security measures are implemented to prevent or minimize the likelihood and impact of risks.
- Detect – Risk events and incidents are identified and analyzed in a timely manner.
- Respond – Actions are taken to remediate or resolve the negative impact of an incident.
- Recover – Operations and assets affected by the incident are restored promptly.
These functions are further divided into 22 categories and 106 subcategories, detailing the specific controls that organizations can implement to safeguard their technology infrastructures. NIST CSF controls range from administrative controls such as risk assessment and cybersecurity training, operational controls like incident response plans, to technical controls such as data security and access control.
What are the NIST CSF maturity levels?
Aside from the Core Functions, other components of the NIST Cybersecurity Framework include Organizational Profiles and Tiers. Organizational Profiles consist of directives on how an organization can create its Current Profile and Target Profile, which describe its existing and desired cybersecurity posture based on achieved and intended outcomes.
The CSF Tiers, on the other hand, help organizations evaluate the maturity of their cybersecurity risk governance and management practices, as well as the processes they have in place. These Tiers are comprised of four maturity levels:

1. Partial
A partial cybersecurity risk management implementation is characterized by an informal, ad hoc response to risk. At this level, your organization has limited awareness of cybersecurity, operational, and third-party risks and risk management is implemented on a case-by-case basis, making it difficult to identify, prioritize, mitigate, and monitor risks effectively. Organizations at this maturity level require a structured cybersecurity risk management program with comprehensive policies and controls and standardized processes.
2. Risk-informed
Meanwhile, organizations with a risk-informed approach to cybersecurity have risk governance and management practices in place. At this maturity level, organizations transition from a reactive to a more proactive approach to risk management. However, risk management is not fully operationalized across all levels of the organization, potentially involving the lack of oversight of risks associated with suppliers, vendors, and other third parties. There is risk awareness in the organization but risk information is shared inconsistently or informally. Risk assessment procedures are present but not conducted regularly.
3. Repeatable
The next level of cybersecurity maturity encompasses standardized and consistent risk management practices that are not only implemented but also enforced as policies across an organization. Organizations at this level progress from a risk-informed strategy to adopting robust and repeatable methods. Risk management policies, processes, and procedures are well-documented, functioning as intended, and regularly reviewed and updated based on changes in the organization’s business objectives and threat landscape. Risk information is routinely shared throughout the organization, relevant personnel are adequately trained, and cybersecurity risks are considered by top management in all areas of operation, including third-party engagements.
4. Adaptive
Finally, the highest level of cybersecurity maturity that an organization can attain involves an agile, risk-informed, and continuously improving risk management strategy. At this level, organizations have evolved from risk awareness to a comprehensive and continuous response in which risk management is integrated into the cultural framework of the organization. Current and predicted cybersecurity risks dictate budgets and business objectives and are factored into decision-making processes. In return, business units execute the organization’s risk strategy based on executive vision and risk tolerance. Organizations with an adaptive maturity level can dynamically adjust to changes in risks and business goals and quickly deploy measures to address new challenges.
All in all, gaining a deep understanding of these maturity levels and determining where your organization stands is crucial in validating your cybersecurity readiness and operational resilience.






