Aligning your organization with in-demand cybersecurity frameworks safeguards your data, systems, and operations from diverse threats, helping you secure your business and foster sustainability. The National Institute of Standards and Technology or NIST offers several compliance frameworks that organizations can use to guide their security and risk management practices. This article will explore these frameworks and why organizations should adopt them, and provide a step-by-step guide on how you can build a robust security program and become NIST-certified. Learn more below:
What does it mean to be NIST-certified?
Being NIST-certified simply means being compliant with any of the frameworks or publications released by NIST. This involves going through the NIST compliance process, which includes implementing specific requirements, preparing the necessary documentation that details your organization’s security measures, and undergoing an external audit to verify your compliance.
NIST is a US federal agency that develops standards and measurement solutions to support technological innovation, economic security, and industrial competitiveness. While compliance with NIST frameworks is voluntary for organizations, it is mandatory for government agencies as well as contractors and service providers handling federal information.
Demonstrating your compliance with NIST frameworks offers many advantages to your organization. Aside from providing a structure for your security program, it allows you to:
- Identify your assets as well as system vulnerabilities and internal and external risks that could significantly impact them
- Establish policies, procedures, and controls to safeguard these assets and prevent or reduce the likelihood of incidents
- Evaluate the maturity of your security program to implement improvements or corrective measures
- Prioritize and prove your commitment to cybersecurity and information security to increase stakeholder trust
In essence, being NIST-compliant enables you to be well-equipped to take on various threats ranging from cyberattacks to natural disasters, empowering your organization to thrive in a dynamic digital landscape.
3 types of NIST compliance frameworks
To start your journey to NIST compliance, first you need to select a framework that best suits your organization. Here are a few of the most popular NIST frameworks you can choose from:
NIST CSF
The NIST Cybersecurity Framework (NIST CSF) provides guidelines for managing cybersecurity risks through 6 functions: Govern, Identify, Protect, Detect, Respond, and Recover. It contains best practices and controls that organizations can adopt to achieve their desired cybersecurity outcomes, covering domains such as developing a cybersecurity policy, asset management and risk assessment, access control, incident response and recovery, among others.
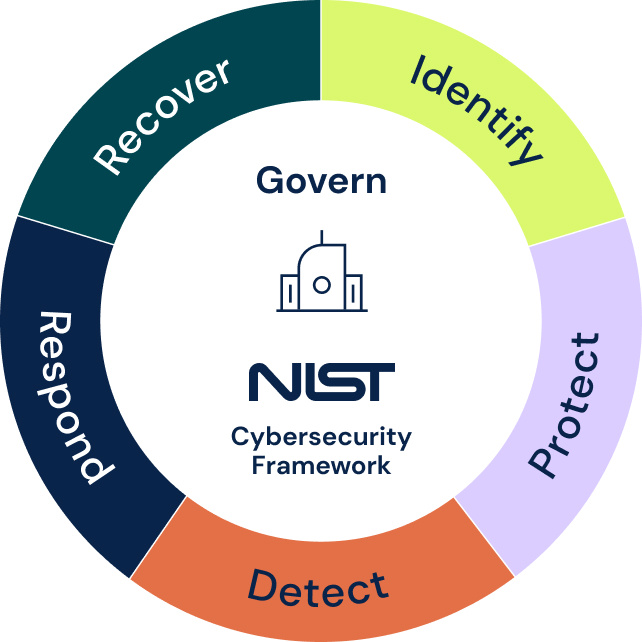
According to the 2017 Executive Order 13800, NIST CSF is mandatory for US government agencies. For other organizations, compliance with NIST CSF can help you develop minimum security measures to become compliant with the requirements of other laws and regulations. These include the US Sarbanes–Oxley Act (SOX) and the EU Digital Operational Resilience Act (DORA) for financial institutions, the Health Insurance Portability and Accountability Act (HIPAA) for healthcare providers, and the General Data Protection Regulation (GDPR).
NIST SP 800-53
The NIST Special Publication 800-53 outlines a catalog of security and privacy controls for the protection of federal information systems and organizations against diverse risks. Its controls are divided into 20 control families or categories such as audit and accountability, contingency planning, incident response, system and communications protection, and more. Prior to implementing these controls, a risk management framework must be established following the steps detailed in the NIST Risk Management Framework (RMF).

NIST SP 800-53 is designed to fulfill the requirements of the Federal Information Security Modernization Act (FISMA) and the Federal Information Processing Standards (FIPS) for safeguarding government information and operations, making compliance mandatory for US government departments and agencies as well as for contractors working with them.
NIST SP 800-171
On the other hand, the NIST Special Publication 800-171 deals with safeguarding the confidentiality of sensitive government data or Controlled Unclassified Information (CUI). It provides a set of security requirements for non-federal systems and organizations that process, store, and transmit CUI. NIST SP 800-171 contains most of the same control families from NIST SP 800-53, excluding contingency planning, program management, and personally identifiable information (PII) processing and transparency.

Contractors for the US Department of Defense are required to implement the security requirements of NIST SP 800-171 to demonstrate their capacity to protect federal information in compliance with the Federal Acquisition Regulation (FAR) and the Defense Federal Acquisition Regulation Supplement (DFARS). NIST SP 800-171 is also mandatory for manufacturers or service providers that are part of the supply chain of federal or state agencies.
6 steps in the NIST compliance process
The process of becoming NIST-compliant involves a combination of preparation, implementation, and monitoring. Here are the steps you can follow to achieve NIST compliance:
1. Assess your security posture
Before implementing the requirements or controls of any of the NIST frameworks above, you first need to evaluate your current security posture and identify any gaps or vulnerabilities that you need to address. For organizations lacking a basic security program, opting for NIST CSF is ideal, while NIST SP 800-53 and SP 800-171 are more appropriate for those with a solid security framework in place.
2. Establish a risk management framework
Once you have determined the vulnerabilities that present risks to your assets, operations, and other critical aspects of your organization, you can proceed to create a plan on how to remediate them using risk management frameworks such as the NIST RMF. With a risk management framework, your organization can put in place processes for identifying, assessing, prioritizing, mitigating, and monitoring risks.
Risk assessment and a risk management strategy are significant components of all three NIST frameworks, requiring organizations to define policies and procedures for risk assessment, determine the likelihood and impact of risks, and document and communicate risk assessment results.
To make way for a more efficient risk assessment process, use 6clicks’ comprehensive risk registers with custom risk fields, automatic risk rating calculation, and task management features to streamline your workflow. You can also leverage data visualization tools such as risk matrices and presentations powered by 6clicks LiveDocs and instantly generate reports to unlock insights into your risk management activities.

3. Set up NIST controls
Now, it’s time to set up the security controls specified in the NIST framework applicable to your organization. This involves implementing different types of security measures, from administrative to technical and physical controls, to prevent or reduce risks. Establishing roles, responsibilities, and authorizations, data encryption, patch management, and conducting security training are just some of the NIST controls that must be part of your security framework.
It is important to note that although NIST SP 800-53 and SP 800-171 share similar control families, there are distinct nuances to the controls in each framework. For example, NIST SP 800-53 provides a detailed list of controls under access control, including restrictions on the use of shared and group accounts, attribute-based access control, and flow control of encrypted information. Meanwhile, NIST SP 800-171 features more general guidelines such as access control for mobile devices, least privilege, and account management.
6clicks’ control management functionality enables you to easily set up controls and assign control tasks to team members to ensure your organization’s compliance. Then, conduct tests to check the effectiveness of your controls through 6clicks’ Continuous Control Monitoring feature. You can also use our AI engine Hailey to automate the mapping of your controls to the provisions of your chosen NIST framework, making it easier to assess your level of compliance.

4. Validate controls through internal audits
With security controls in place and NIST requirements fulfilled, performing an internal audit to examine the components of your security program and validate your compliance is the next step in the process. Internal audits help you identify non-conformities and areas of non-compliance so you can initiate remediation.
Through 6clicks’ Audit & Assessment capability, you can automate audits using turnkey question-based and requirement-based assessment templates and quickly identify risks and issues from assessment responses using Hailey. Continuous control monitoring also enables you to detect control failures and security incidents in real time, allowing you to promptly action issues within 6clicks’ integrated Issue & Incident Management module.
5. Complete an external NIST audit
To finally verify your NIST compliance, your organization must undergo a structured and comprehensive external audit performed by an independent third-party auditor. For this, you need to prepare internal audit records and other relevant documentation to prove your compliance. You can seamlessly export these documents as well as reports on control performance using 6clicks’ built-in Reporting & Analytics feature.
While there are no formal certifications issued for NIST frameworks, you can seek certifications such as FISMA, the Cybersecurity Maturity Model Certification (CMMC), and the Federal Risk and Authorization Management Program (FedRAMP) to demonstrate your compliance with NIST SP 800-53 and SP 800-171.
6. Monitor compliance
Lastly, enforcing monitoring mechanisms is crucial for maintaining compliance. Continuous monitoring is a recurring theme in all NIST frameworks, urging organizations to ensure rigorous surveillance of their security controls to stay ahead of threats and maintain a consistent security posture. To achieve this, organizations must employ continuous monitoring systems and conduct regular internal audits and penetration testing to continuously improve their security measures and reach ongoing compliance.
Simplify NIST compliance with 6clicks
Get NIST-compliant fast with 6clicks’ AI-powered cyber GRC platform with integrated risk management, security compliance, and audit & assessment capabilities. Explore our NIST CSF solution which includes ready-to-use control sets and assessment templates to streamline your compliance.
Frequently asked questions
What are NIST SP 800-53 and SP 800-171?
NIST special publications 800-53 and 800-171 are both security frameworks that outline mandatory controls for managing risks and safeguarding government information and operations. NIST SP 800-53 focuses on security measures for federal information systems and organizations while NIST SP 800-171 mandates requirements for non-federal organizations and contractors handling federal information.
What is the NIST compliance process?
Becoming NIST-compliant is a comprehensive process that encompasses assessing your security readiness prior to adopting a NIST framework, developing a risk management framework, implementing NIST security controls, and going through internal and external audits to confirm your compliance. Continuous monitoring is also necessary to maintain robust security and remain compliant.
Can you acquire a NIST certification?
There are no direct certifications for NIST but you can get certified in other programs such as the Cybersecurity Maturity Model Certification (CMMC) and the Federal Risk and Authorization Management Program (FedRAMP) which provide requirements that align with NIST SP 800-53 and SP 800-171 controls.
Written by Jami Samson
Jami is a seasoned Technical Writer at 6clicks, where she harnesses her extensive experience in domains such as information technology, artificial intelligence, and GRC to craft high-quality content. Having worked in the marketing field since 2017, she has established a solid background in copywriting and content writing and is skilled in translating complex topics into informative and engaging pieces. Apart from writing, Jami is also passionate about music.









