At 6clicks, our relentless pursuit is to streamline processes and enhance efficiency through meticulous automation. Our latest advancement in process automation for audits and risk assessments, unveiled just before the 2021 holidays, exemplifies this commitment.
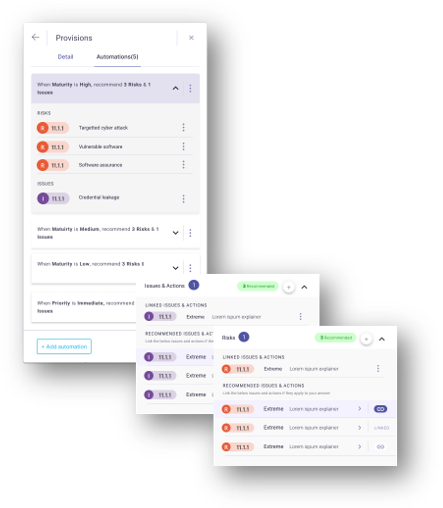
Picture this: A customizable library encompassing risks, issues, actions, and treatment plans. With each audit or risk assessment response, you dictate the relevant risks and issues to consider. When the assessment aligns with this template, a seamless triage of risks and issues is triggered, eliminating the need for an exhaustive result review.
Welcome to the future powered by 6clicks.
Simplify assessments:
- Link risks and issues to assessment responses.
- Conduct the assessment.
- Watch 6clicks intelligently suggest risks and issues.
- Automatically generate risks and issues in bulk after assessment.
With a one-time template setup, repetitive recommendations and manual risk creation are things of the past.
Experience heightened operationalized and standardized risk assessments with 6clicks. Your journey to efficiency begins here.
Check it out:
Curious about learning more? Check out our wealth of content in our 6clicks Knowledge Base below.
Automated Risks and Risk Treatment Plans
Automated Issues and Issue Actions
Written by Heather Buker
Heather has been a technical SME in the cybersecurity field her entire career from developing cybersecurity software to consulting, service delivery, architecting, and product management across most industry verticals. An engineer by trade, Heather specializes in translating business needs and facilitating solutions to complex cyber and GRC use cases with technology. Heather has a Bachelors in Computer Engineering, Masters in Engineering Management, and a Doctorate in Information Technology with a specialization in information assurance and cybersecurity.










