Cyber Risk Management Expert Guide
Master cyber risk management with our expert guide! Learn how to identify, evaluate, and address cybersecurity threats using ISO 31000 principles. Access a turn-key cyber risk library and discover how to streamline risk assessments. Download now!
-1.png?width=200&height=249&name=Group%20193%20(1)-1.png)
Cyber Risk Management Expert Guide
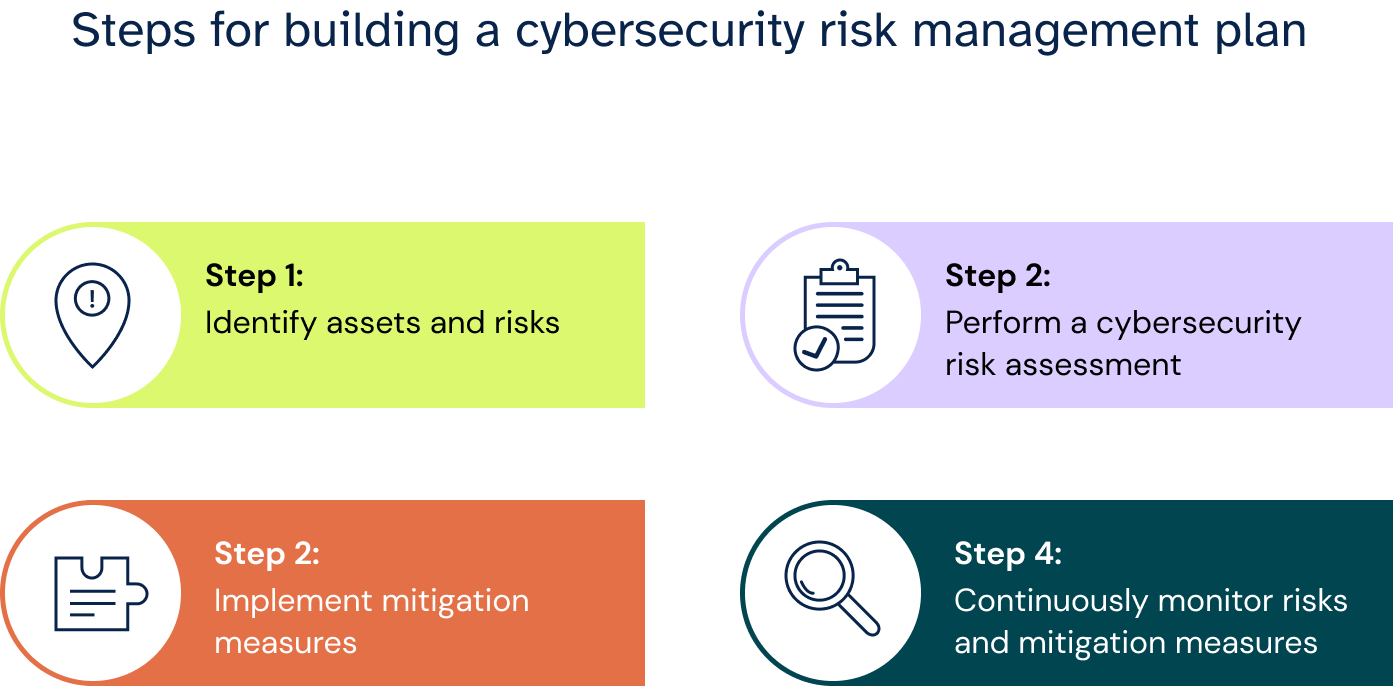
What is cybersecurity risk?
What are the four cybersecurity risk treatment mitigation methods?
The four cybersecurity risk treatment mitigation methods are essential strategies organizations use to effectively manage and address potential cyber threats. Based on the ISO 31000 risk management framework, these methods play a critical role in safeguarding sensitive data and digital operations.
1. Risk avoidance
- Example: An organization might decide not to store sensitive customer data in cloud environments to eliminate the risk of data breaches.
- Another example: Avoiding the use of outdated software that is prone to vulnerabilities.
Risk avoidance in cyber security helps organizations proactively eliminate potential threats, forming a vital part of a comprehensive cybersecurity strategy.
2. Risk reduction (mitigation)
- Example: Deploying multi-factor authentication, implementing firewalls, and conducting regular software updates to address vulnerabilities.
- When to use: When risks cannot be completely avoided but can be minimized effectively.
Risk mitigation in cyber security is widely used to ensure that even if a threat materializes, its impact is controlled and manageable.
3. Risk sharing (transfer)
- Example: Purchasing cyber liability insurance to cover financial losses from data breaches or outsourcing security monitoring to a third-party provider.
- When to use: When an organization prefers to share the financial or operational burden of a specific risk.
4. Risk acceptance
- Example: Accepting low-priority risks for non-critical systems that are unlikely to cause significant damage.
Why risk avoidance and risk mitigation matter in cyber security
Understanding what is risk avoidance in cyber security and what is risk mitigation in cyber security enables organizations to take a proactive and balanced approach to managing cyber threats. While risk avoidance eliminates potential threats entirely, risk mitigation ensures that threats are controlled and their impacts minimized. Together, these strategies contribute to a robust cybersecurity defense.
Summary of cybersecurity risk treatment methods
| Method | Action | Example in cyber security |
| Risk avoidance | Eliminate the risk entirely | Avoid storing sensitive data online |
| Risk reduction | Minimize likelihood or impact | Install firewalls and update systems |
| Risk sharing | Transfer the risk to another entity | Buy cyber insurance or outsource IT |
| Risk acceptance | Accept the risk without further action | Acknowledge low-priority risks |
By incorporating risk avoidance and risk mitigation strategies, organizations can proactively protect their digital assets while balancing operational needs. These methods, alongside risk sharing and acceptance, form a comprehensive framework for effective cybersecurity risk management.
Discover the AI's impact on cybersecurity here.
How 6clicks can help
- Powerful risk register to record, evaluate, and categorize risks based on criticality
- Customizable data fields and workflows to streamline the risk assessment process
- Task assignment features for facilitating risk treatment
- AI-powered risk creation using 6clicks Hailey





.png?width=302&height=170&name=The%20Future%20of%20Cyber%20GRC%20Expert%20Guide%20eBook%20(2).png)






